PQC with Caddy 2.10

You might have noticed that PQC has become a (really) hot topic in the past few weeks, and to be honest, I don’t know why—since we are years away from a “real-life” cryptographic doomsday. I quote the NIST :
Researchers need to surmount many technical challenges before this can happen. Experts’ estimates range from a few years to a few decades.
However, just because PQC is still years away from being a matter of life and death doesn’t mean we should wait before toying with it or starting to use it. I’m not sure one should use it on mission-critical services yet, as the devil hides in bugs, and it’s wayyyy too early to have enough feedback on PQC algorithm implementations. But because I like to be on zee bleeding edge, I decided to activate support for PQC for this blog. It is totally useless —therefore, totally necessary!
And because I run Alpine Linux on zee bleeding edge also, I can benefit from Caddy 2.10…
arkham:~$ cat /etc/alpine-release
3.23.0_alpha20250612
arkham:~$ caddy --version
v2.10.0So for my configuration, it is as simple as setting x25519mlkem76 for the curves options
opium.io {
root * /lighttpd-jail
encode gzip
file_server
tls {
curves x25519mlkem768 secp384r1 secp256r1 x25519
}
header {
Strict-Transport-Security "max-age=31536000;"
X-Content-Type-Options "nosniff"
X-Frame-Options "SAMEORIGIN"
X-XSS-Protection "1; mode=block"
Content-Security-Policy "script-src 'self'"
Referrer-Policy "no-referrer-when-downgrade"
}
log {
output file /var/log/access.log
}
}Restart Caddy and voilà!
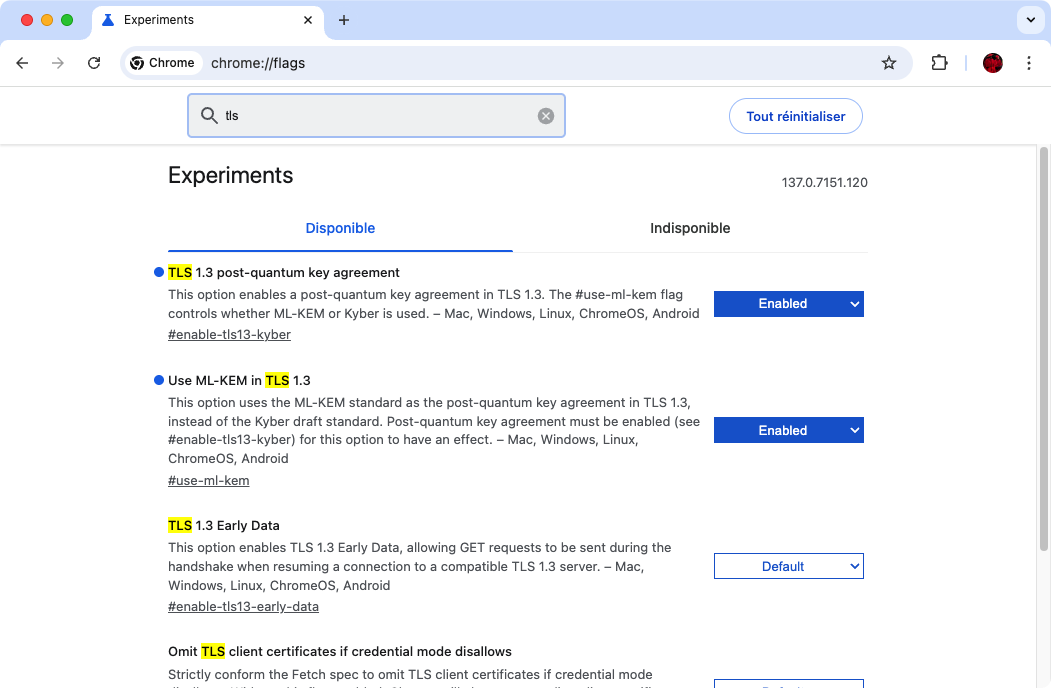
Sadly even Chrome does not support PQC by default as of today… So you have to activate it in chrome://flags/ and search for tls
Restart Chrome, open the developper tools and hold and behold!
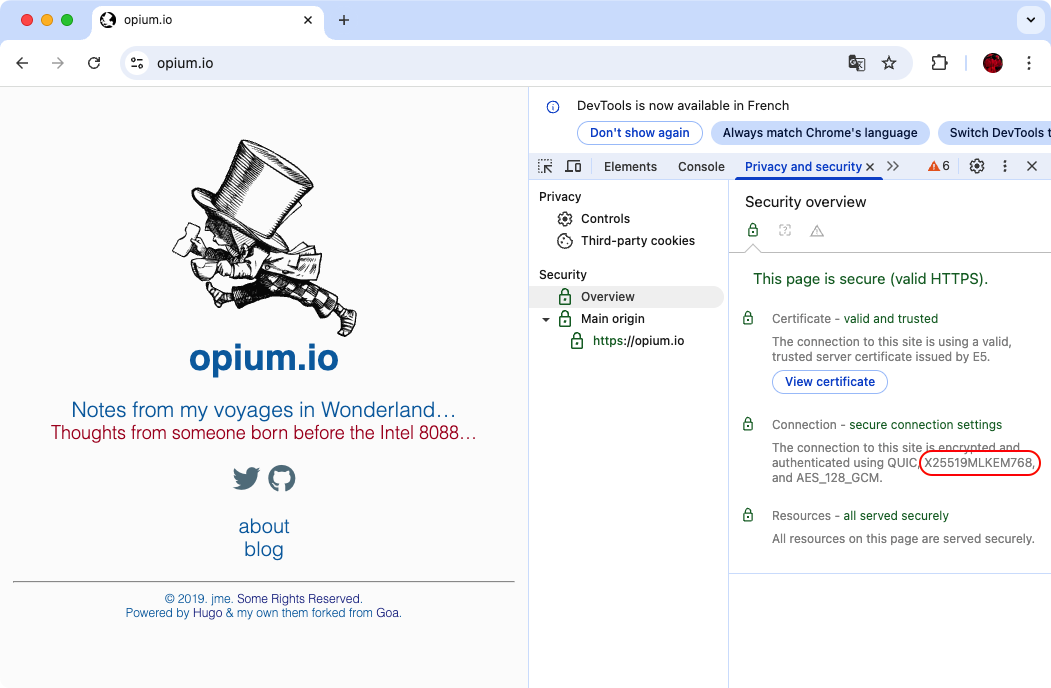
Sadly, you will see that the cipher is AES_128_GCM. Grover’s Algorithm halves the effective key lenght of symmetric key algorithms (AES in this case). So Since RFC 8446 requires TLS_AES_128_GCM and because Go’s stdlib for TLS doesn’t allow configuring cipher suites and order… you get a PQC web server not totally PQC proof…
But I’m no cryptographer so I might be wrong :)
This blog post is 100% human-written and 100% GenAI proofread.